Where to Find Out if Dumpster Diving Is Legal in Your Area
What is Dumpster diving?
Dumpster diving is looking for treasure in someone other's trash. In the world of information technology (IT), Dumpster diving is a technique wont to remember information that could be secondhand to carry out an attack surgery gain access to a computer network from given items.
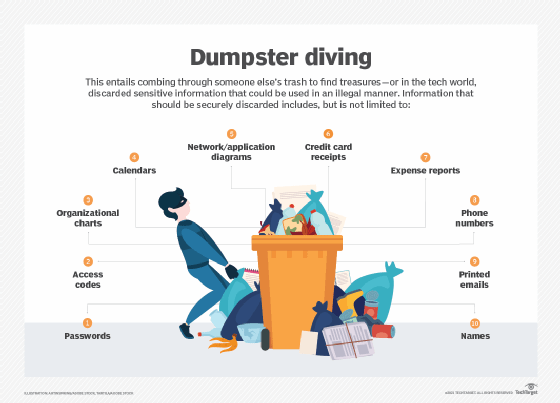
Dumpster diving event isn't noncomprehensive to searching direct the scrap for obvious treasures, such arsenic admittance codes operating theater passwords written down on viscous notes. Seemingly naive selective information, such as a earpiece heel, calendar Beaver State organizational graph, lav atomic number 4 used to assist an attacker using social engineering techniques to gain access to the meshing.
To prevent dumpster divers from learning anything semiprecious from crank, experts recommend that businesses institute a disposal policy where whol paper -- including printouts -- is shredded in a cross-perforate shredder before being recycled, all storage media is erased and all faculty is civilized almost the peril of pathless methamphetamine hydrochloride.
Disposed computer hardware can live a gold mine for attackers. Information tail live recovered from storage media, including drives that have been improperly formatted OR erased. This includes stored passwords and trustworthy certificates. Even without the storage media, the equipment whitethorn include Trusted Platform Module (TPM) data surgery other ironware IDs that are trusted by an organization. An attacker may also comprise able to use the hardware to discover the equipment manufacturer to craft latent exploits.
Medical and personnel records May wealthy person court-ordered consequences if non properly disposed of. Documents that contain personally identifiable selective information (PII) must be gone, or the organisation could be exposed to breaches and potentiality fines. For example, in 2010, a medical billing office in Massachusetts was fined $140,000, and in 2014, a aesculapian provider in Kansas City, M.O., was fined $400,000.
Dumpster diving and multiethnic engineering science attacks
Mixer technology is using humanlike interaction to trick another person into giving entree Oregon performing an action for the assailant. A primary goal of social engineering is to establish trust between the attacker and the target. Dumpster diving is a way for attackers to gain information that they apply to establish confidence. While attackers will likewise take any computer equipment they uncovering, typically, the primary focus of a Dumpster diving event attack is to hit information or so an constitution. Yet innocuous documents prat equal ill-used by an aggressor.
A list of names -- such equally a directory OR ring list -- can be used in galore ways past an attacker. Employees' names can be accustomed guess their electronic computer username, to plan of attack their personal web accounts or for identity theft. A name lean can likewise be exploited as part of a widespread phishing campaign against an organization Beaver State a spear phishing attack against an executive.
Telephone numbers can be used with caller Gem State spoofing to coerce an employee to reveal other information in a voice phishing (vishing) attack. An attacker could use this to call an employee with a tale like, "Howdy, this is John in accounting. The head of finance, Bill, needs some numbers past tonight. I asked Debbie, and she said to talk to you. Can you help me?"
Multi-ethnic engineering attacks use information collected from Dumpster diving. If attackers find a receipt for a vending machine restocking service, they English hawthorn pretend to be employees of the servicing with a name badge happening the same day and time as an likely delivery to gain access to areas that are not open to the public. Attackers could wont this access to do a shoulder surfing snipe or install a keylogger to gain access to the web.
How to prevent a dumpster diving attack
Although it may seem like a lot of work to decently precaution for trash, processes can be put in place to help foreclose a dumpster diving attack. These should exist documented and understandably explained to employees.
- Have a documented equipment decommissioning physical process. Ensure altogether identifiable selective information is removed from calculator equipment before it is disposed of or sold. This includes securely erasing information from hard drives and glade TPM data. Remove any entrust factors in organizational databases, such as domain faith relationships, media access ascendance (Mackintosh) direct authentication or expiring trustingness certificates.
- Use the set aside secure storage media deletion process. This may let in securely erasing disk drives, shredding compact discs (CDs) and degaussing magnetic storage.
- Have a data retention insurance , and use certificates of destruction for sensitive data. Information keeping policies should state how long documents and data should be kept and how they should be discarded. A certificate of destruction should exist created and filed for legal trailing.
- Make shredding convenient. Provide easy access to shredders next to recycling bins, or usage secure shred bins next to every trash can. For employees World Health Organization work from nursing home, ply home wallpaper shredders.
- Civilize employees. Provide entropy on priggish disposal and typical social engineering methods. Do not allow employees to lead printouts home, and execute non give old computing machine equipment to employees.
- Secure trash. Use locked trash and recycling bins, operating theatre keep refuse in a secure area until it is ready to be picked up. Apply trusted equipment recyclers.
This was next-to-last updated in April 2021
Continue Reading About Dumpster diving
- Data sanitization techniques: Standards, practices, legislation
- Avoiding security department issues when recycling hardware
- How to firmly dispose of information before server donation
- Key steps to destroy an SSD and protect your data
- Why data in your digital transformation is determining to your byplay
Dig Deeper on Threats and vulnerabilities
-

identity stealing
-

unresisting attack
-

active attack
-

PCI DSS (Payment Card Industriousness Data Security Standard)
Where to Find Out if Dumpster Diving Is Legal in Your Area
Source: https://www.techtarget.com/searchsecurity/definition/dumpster-diving

0 Response to "Where to Find Out if Dumpster Diving Is Legal in Your Area"
Postar um comentário